Google Analytics Certification Exam: Get Certified in 2 Days
A year ago I felt a panic that still reverberates in me today. Hackers swapped my T-Mobile SIM card without my approval and methodically shut down access to most of my accounts and began reaching out to my Facebook friends asking to borrow crypto. Their social engineering tactics, to be clear, were laughable but they could have been catastrophic if my friends were less savvy.
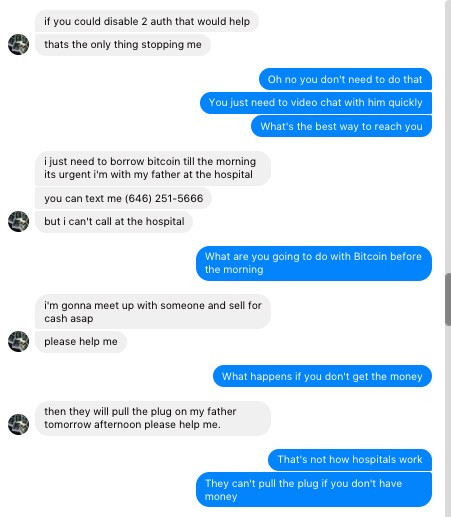
Flash forward a year and the same thing happened to me again – my LTE coverage winked out at about 9pm and it appeared that my phone was disconnected from the network. Panicked, I rushed to my computer to try to salvage everything I could before more damage occurred. It was a false alarm but my pulse went up and I broke out in a cold sweat. I had dealt with this once before and didn’t want to deal with it again.
Sadly, I probably will. And you will, too. The SIM card swap hack is still alive and well and points to one and only one solution: keeping your crypto (and almost your entire life) offline.
Trust No Carrier
Stories about massive SIM-based hacks are all over. Most recently a crypto PR rep and investor, Michael Terpin, lost $24 million to hackers who swapped his AT&T SIM. Terpin is suing the carrier for $224 million. This move, which could set a frightening precedent for carriers, accuses AT&T of “fraud and gross negligence.”
From Krebs:
Terpin alleges that on January 7, 2018, someone requested an unauthorized SIM swap on his AT&T account, causing his phone to go dead and sending all incoming texts and phone calls to a device the attackers controlled. Armed with that access, the intruders were able to reset credentials tied to his cryptocurrency accounts and siphon nearly $24 million worth of digital currencies.
While we can wonder in disbelief at a crypto investor who keeps his cash in an online wallet secured by text message, how many other services do we use that depend on emails or text messages, two vectors easily hackable by SIM spoofing attacks? How many of us would be resistant to the techniques that nabbed Terpin?
Another crypto owner, Namek Zu’bi, lost access to his Coinbase account after hackers swapped his SIM, logged into his account, and changed his email while attempting direct debits to his bank account.
“When the hackers took over my account they attempted direct debits into the account. But because I blocked my bank accounts before they could it seems there are bank chargebacks on that account. So Coinbase is essentially telling me sorry you can’t recover your account and we can’t help you but if you do want to use the account you owe $3K in bank chargebacks,” he said.
[gallery ids="1695834,1695835"]Now Zu’bi is facing a different issue: Coinbase is accusing him of being $3,000 in arrears and will not give him access to his account because he cannot reply from the hacker’s email.
“I tried to work with coinbase hotline who is supposed to help with this but they were clueless even after I told them that the hackerchanged email address on my original account and then created a new account with my email address. Since then I’ve been waiting for a ‘specialist’ to email me (was supposed to be 4 business days it’s been 8 days) and I’m still locked out of my account because Coinbase support can’t verify me,” he said.
It has been a frustrating ride.
“As an avid supporter and investor in crypto it baffles me how one of the market leaders who just supposedly launched institutional grade custody solutions can barely deal with a basic account take-over fraud,” Zu’bi said.
How do you protect yourself?
I’ve been using Trezor hardware wallets for a while, storing them in safe places outside of my home and maintaining a separate record of the seeds in another location. I have very little crypto but even for a fraction of a few BTC it just makes sense to practice safe storage. Ultimately, if you own crypto you are now your own bank. That you would trust anyone – including a fiat bank – to keep your digital currency safe is deeply delusional. Heck, I barely trust Trezor and they seem like the only solution for safe storage right now.
When I was first hacked I posted recommendations by crypto exchange Kraken. They are still applicable today:
Call your telco and:
-
Set a passcode/PIN on your account
- Make sure it applies to ALL account changes
- Make sure it applies to all numbers on the account
- Ask them what happens if you forget the passcode
- Ask them what happens if you lose that too
-
Institute a port freeze
-
Institute a SIM lock
-
Add a high-risk flag
-
Close your online web-based management account
-
Block future registration to online management system
-
Hack yo’ self
-
See what information they will leak
-
See what account changes you can make
-
They also recommend changing your telco email to something wildly inappropriate and using a burner phone or Google Voice number that is completely disconnected from your regular accounts as a sort of blind for your two factor texts and alerts.
Sadly, doing all of these things is quite difficult. Further, carriers don’t make it easy. In May a 27-year-old man named Paul Rosenzweig fell victim to a SIM-swapping hack even though he had SIM lock installed on his account. A rogue T-Mobile employee bypassed the security, resulting in the loss of a unique three character Twitter and Snapchat account.
Ultimately nothing is secure. The bottom line is simple: if you’re in crypto expect to be hacked and expect it to be painful and frustrating. What you do now – setting up real two-factory security, offloading your crypto onto physical hardware, making diligent backups, and protecting your keys – will make things far better for you in the long run. Ultimately, you don’t want to wake up one morning with your phone off and all of your crypto siphoned off into the pocket of a college kid like Joel Ortiz, a hacker who is now facing jail time for “13 counts of identity theft, 13 counts of hacking, and two counts of grand theft.” Sadly, none of the crypto he stole has surfaced after his arrest.
Master Google Adwords like a boss
from Chriss H Feed https://ift.tt/2wgxssf
via IFTTT
No comments:
Post a Comment